Bong the Hackers!!
Table of contents
Implementing Honeypot in our network to monitor incoming network request and interactions, (200 OK) and lets dive into : - ).
Introduction
So hi, If you are here I assume that you wanna learn how to catch some cyber criminals, So you are come to the right place. I'll show you how to create a totally awesome HTTP honeypot in Python that logs attacker data in JSON format using Elasticsearch. And the best part? I'll do it with Little more fun! So sit back, relax, Everything I made It must contain fun in it.
and let's get started on this cyber adventure!
The required building block
Here are the thing you have to need
A Computer. Duh
Python 3.* installed in this
Basic knowledge of the HTTP protocol. We promise we won't get too technical, but it's always good to know what you're working with.
A terminal, get ready by sharping your fingers.
Elastic search and Kibana if its not installed, go and check my next post, but it wasnt published yet 🙂.
Lets Construct
Step 1: Import necessary modules
Let's get down to business! We'll start by importing the modules we'll need for our honeypot. You know, the usual suspects: socket for creating a socket and listening on port 8080, json for converting Python dictionaries to JSON strings, datetime for getting the current date and time, and request modulefor communicating with Elasticsearch.
import socket
import json
import requests
from datetime import datetime
Step2: Define the log request function
Now, here's where the real fun begins. Our log_request function takes the HTTP request and client address as inputs and logs the attacker data in Elasticsearch. But we're not just logging any data, oh no. We're logging the attacker's IP address, port, time, HTTP method, subdomain, and URL. That's right, we're going all out with this honeypot!.
def log_request(request, client_address):
lines = request.split('\r\n')
request_line = lines[0].split()
method, url, _ = request_line
subdomain, _, path = url.partition('/')
data = {
'time': str(datetime.now()),
'attacker_ip': client_address[0],
'attacker_port': client_address[1],
'method': method,
'subdomain': subdomain,
'url': path,
}
with open('log.json', 'a') as f:
f.write(json.dumps(data) + '\n')
url = "http://localhost:9200/http/_doc"
headers = {"Content-Type": "application/json"}
global response
response = requests.post(url, headers=headers, json=data)
print(response.status_code)
This code will get the HTTP logs and convert it into JSON format and forward it into elasticsearch "http" index.
"http://localhost:9200/http/_doc"
and create the start server function() to start the server to listen on the port 8080 and push the json data to Elastic with request function.
Let's start the Honeypot and wait for the incoming connection.
#python3 honeypot.py
Listening on 0.0.0.0:8080...........
If we try to connect the web server 172.16.16.220:8080
Hurray!!! we got the logs of the attacker in out elastic search

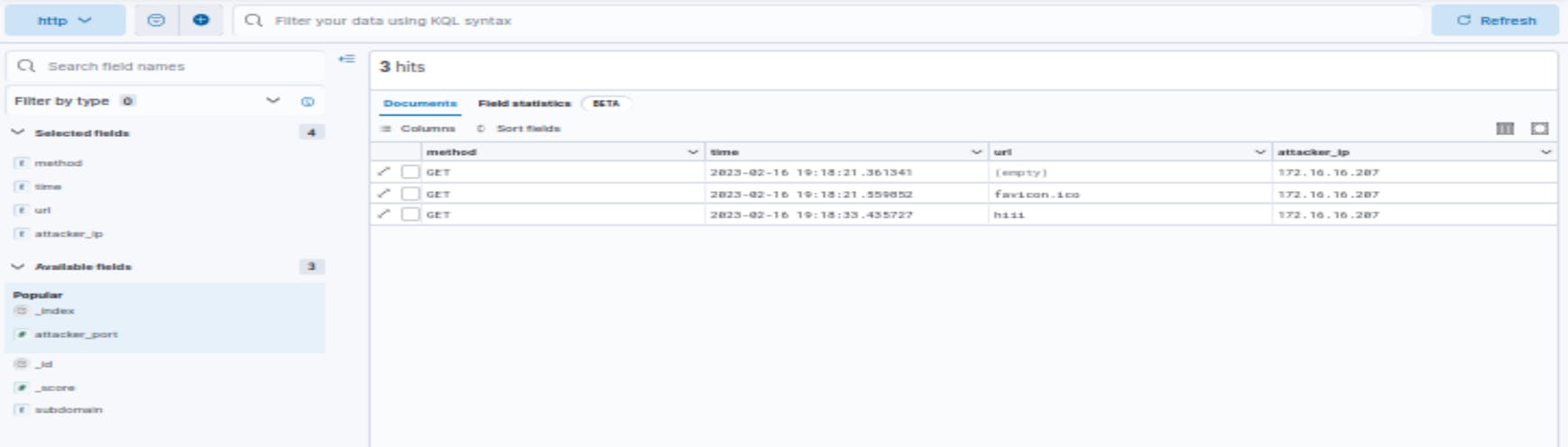
It will list all the activities of the Attacker in our elastic search
Get that code in my github repo https://github.com/Rooban-Prakash/Honeypot-http